Checkov Nedir ?
Checkov, güvenlik veya uyumluluk sorunlarına yol açabilecek hatalı yapılandırmaları tespit etmek için altyapı kod (IaC) dosyalarını tarayan statik bir kod analiz aracıdır. Checkov, yaygın hatalı yapılandırma sorunlarını kontrol etmek için 750’den fazla önceden tanımlanmış politika içerir. Checkov ayrıca özel politikaların oluşturulmasını ve eklenmesini de destekler .
Checkov özellikleri
- Birden fazla sağlayıcı tarafından sağlanan IAC’nizi tarama yeteneği, yani yalnızca Terraform kodunu değil, aynı zamanda CloudFormation, Kubernetes, ARM Templates, Serverless Framework, Dockerfile, GitHub Actions, Python,Helm grafiklerini vb. de tarar.
- Kodunuzu taramak için 1000’den fazla politika.
- Tarama sonuçlarını CLI yerine JUnit ve diğer araçlar aracılığıyla görselleştirme yeteneği.
- Kurulumu kolaydır. Kurulum için sadece pip’e ihtiyacınız var.
- Belirli durumları atlamak istediğinizde sonuçları filtrelemek kolaydır.
IAC Güvenliği
IaC kuruluşumuza önemli bir değer katarken, hangi operasyonel hususları dikkate almalıyız? En önemlisi, bulut güvenliğinin kritik önemini küçümseyemeyiz.
DevOps uygulamaları geliştikçe, kaynak kodu, yazılım uygulamaları, konteyner imajları ve altyapı kaynakları dahil olmak üzere geliştirme süreçlerimizin tüm yönlerinde kapsamlı tarama olmazsa olmaz hale geldi. Yeni sürümleri üretime dağıtmadan önce bu tarama ne kadar kritik? Günümüzün güvenlik ortamı göz önüne alındığında, kesinlikle olmazsa olmazdır. Güvenlik taraması, üretim sistemlerini tehlikeye atabilecek olası güvenlik açıklarına karşı son savunma hattımızdır. Kod Olarak Altyapı (IaC) da bu gerekliliğin bir istisnası değildir; IaC şablonları ve yapılandırmaları, dağıtım süreçlerimizdeki diğer tüm kritik bileşenlerle aynı titiz güvenlik taramasından geçmelidir.
Desteklenen Frameworkler
Checkov, çeşitli yapılandırma dosyalarını taramanıza olanak tanıyan birden fazla IaC çerçevesini destekler:
- Terraform: .tfdosyalar
- CloudFormation: .jsonve .yamldosyalar
- Kubernetes: .yamldosyalar
- ARM Şablonları: .jsondosyalar
- Sunucusuz Çerçeve: serverless.yml dosyalar
Politikalar ve Uyumluluk
Checkov, ortak uyumluluk çerçeveleri ve güvenlik en iyi uygulamaları için yerleşik politikalar içerir, örneğin:
CIS Benchmarks: İnternet Güvenliği Merkezi’nin güvenlik yönergeleri. AWS Temel Güvenlik En İyi Uygulamaları: AWS’ye özgü güvenlik önerileri.
PCI-DSS, HIPAA, SOC 2: Finansal, sağlık ve genel veri korumasına yönelik uyumluluk çerçeveleri.
Özel Politikalar
Checkov’un politika motorunu kullanarak Python’da özel politikalar da yazabilirsiniz. Bu, IaC dosyalarınızda kuruluşa özgü kuralları uygulamanızı sağlar.
Lab Ortamı
Bu makalede chekov aracının kurulumunu yaptıktan sonra Terraform ile hazırlanmış AWS üzerinde EKS kurulumu yapmaza yarayan içerisinde bir çok modül barındıran bir terraform scripti üzerinde çalıştıracak ve bize verdiği raporu detaylı olarak incliyor olacağız.
Checkov kurulumu
MacOs cihazlar için brew kullanıyorsanız aşağıdaki komutu çalıştırıyoruz.Diğer sistemler için bu kılavuzu kullanınız.
| brew install checkov |
|---|
Versiyon kontrolü yapıyoruz aşağıdaki gibi bir çıktı alıyorsak checkov makinemize yüklendi demektir.
| checkov –version 3.2.450 |
|---|
Terraform versiyon kontrol
terraform --version Terraform v1.12.2 on darwin_arm64
uygulayacağım örneğimde aşağıdaki gibi bir EKS Terraform kodum bulunuyor ve bu kodu tarayarak içerisindeki yapılandırmalarda herhangi bir eksiklik yada zafiyet oluşturabilecek bir config var mı bunu kontrol edeceğim.
├── backend.tf ├── karpenter.tf ├── main.tf ├── outputs.tf ├── plan.json ├── provider.tf ├── README.md ├── remote-state.tf ├── tfplan.json ├── variables.tf └── versions.tf
# Terraform kaynağını başlat terraform init Initializing the backend... Initializing modules... Initializing provider plugins... - terraform.io/builtin/terraform is built in to Terraform - Reusing previous version of hashicorp/cloudinit from the dependency lock file - Reusing previous version of alekc/kubectl from the dependency lock file - Reusing previous version of hashicorp/null from the dependency lock file - Reusing previous version of hashicorp/tls from the dependency lock file - Reusing previous version of hashicorp/time from the dependency lock file - Reusing previous version of hashicorp/aws from the dependency lock file - Reusing previous version of hashicorp/helm from the dependency lock file - Using previously-installed hashicorp/cloudinit v2.3.7 - Using previously-installed alekc/kubectl v2.1.3 - Using previously-installed hashicorp/null v3.2.4 - Using previously-installed hashicorp/tls v4.1.0 - Using previously-installed hashicorp/time v0.13.1 - Using previously-installed hashicorp/aws v5.100.0 - Using previously-installed hashicorp/helm v3.0.2 Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary.
Checkov Scan
Bu adımdan sonra aşağıdaki komutları çalıştırarak checkov kontrolü yapacağız.
#terraform planı oluştur terraform plan --out tfplan.binary #tf.plandosyayı JSON formatına dönüştürün terraform show -json tfplan.binary | jq > tfplan.json
Checkov security check
checkov -f tfplan.json checkov -f tfplan.json --skip-download -o cli
Soft fail check
| checkov -d . –soft-fail-on LOW,CKV_AWS_46 |
|---|
Hard fail check
| checkov -d . –hard-fail-on HIGH,CKV_AWS_8,CRITICAL,MEDIUM |
|---|
Komut çıktısı aşağıdaki gibi olacak.
[ kubernetes framework ]: 100%|████████████████████|[1/1], Current File Scanned=tfplan.json
[ secrets framework ]: 100%|████████████████████|[1/1], Current File Scanned=tfplan.jsonson
_ _
___| |__ ___ ___| | _______ __
/ __| '_ \ / _ \/ __| |/ / _ \ \ / /
| (__| | | | __/ (__| < (_) \ V /
\___|_| |_|\___|\___|_|\_\___/ \_/
By Prisma Cloud | version: 3.2.450
Update available 3.2.450 -> 3.2.461
Run pip3 install -U checkov to update
terraform_plan scan results:
Passed checks: 142, Failed checks: 9, Skipped checks: 0
Check: CKV_AWS_41: "Ensure no hard coded AWS access key and secret key exists in provider"
PASSED for resource: aws.default
File: /tfplan.json:19022-19039
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/secrets-policies/bc-aws-secrets-5
Check: CKV_AWS_41: "Ensure no hard coded AWS access key and secret key exists in provider"
PASSED for resource: aws.virginia
File: /tfplan.json:19039-19055
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/secrets-policies/bc-aws-secrets-5
Check: CKV_AWS_288: "Ensure IAM policies does not allow data exfiltration"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-288
Check: CKV_AWS_287: "Ensure IAM policies does not allow credentials exposure"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844 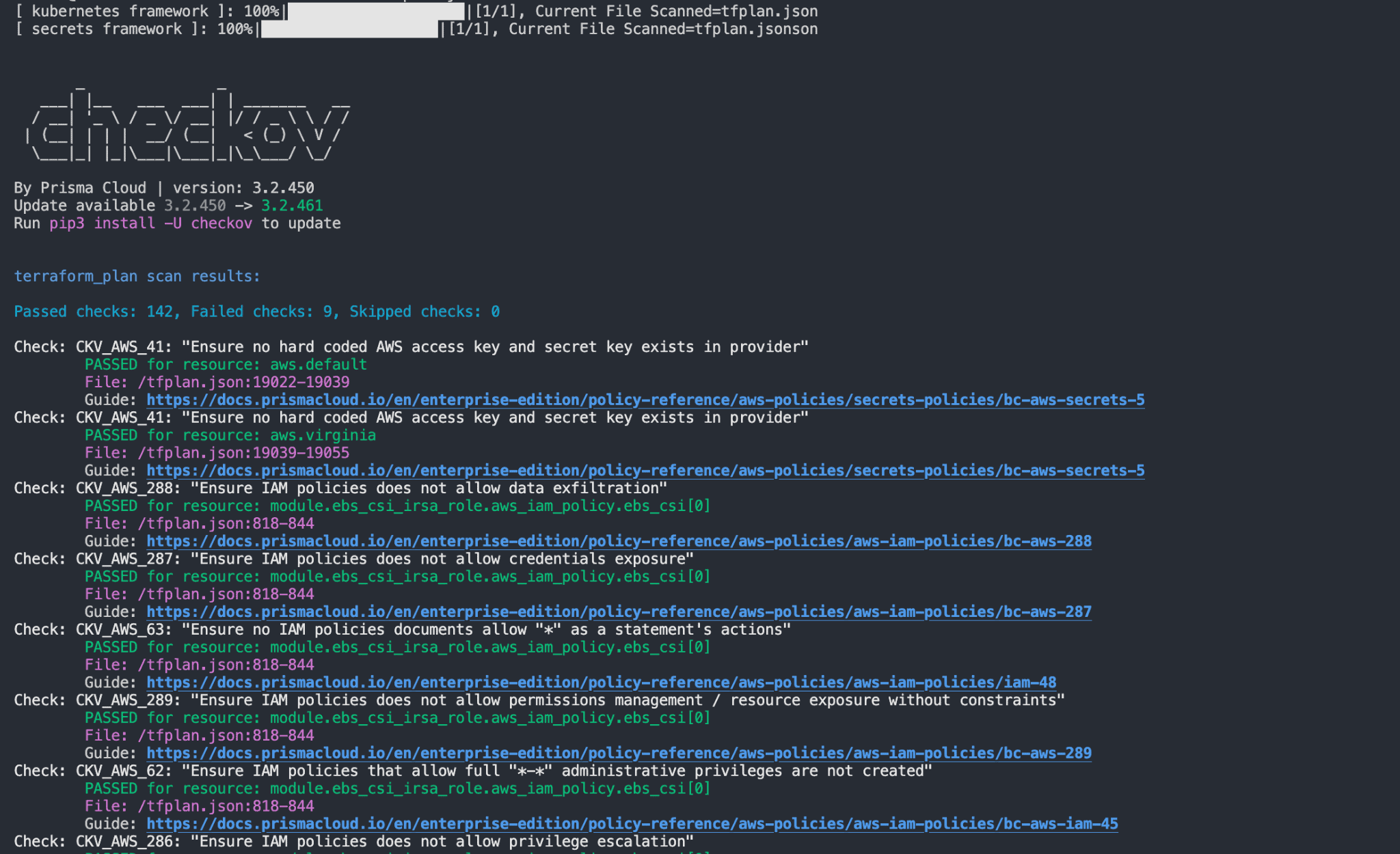
Yapılandırmada hatalı/eksik gördüğü bölümler aşağıdaki gibi.
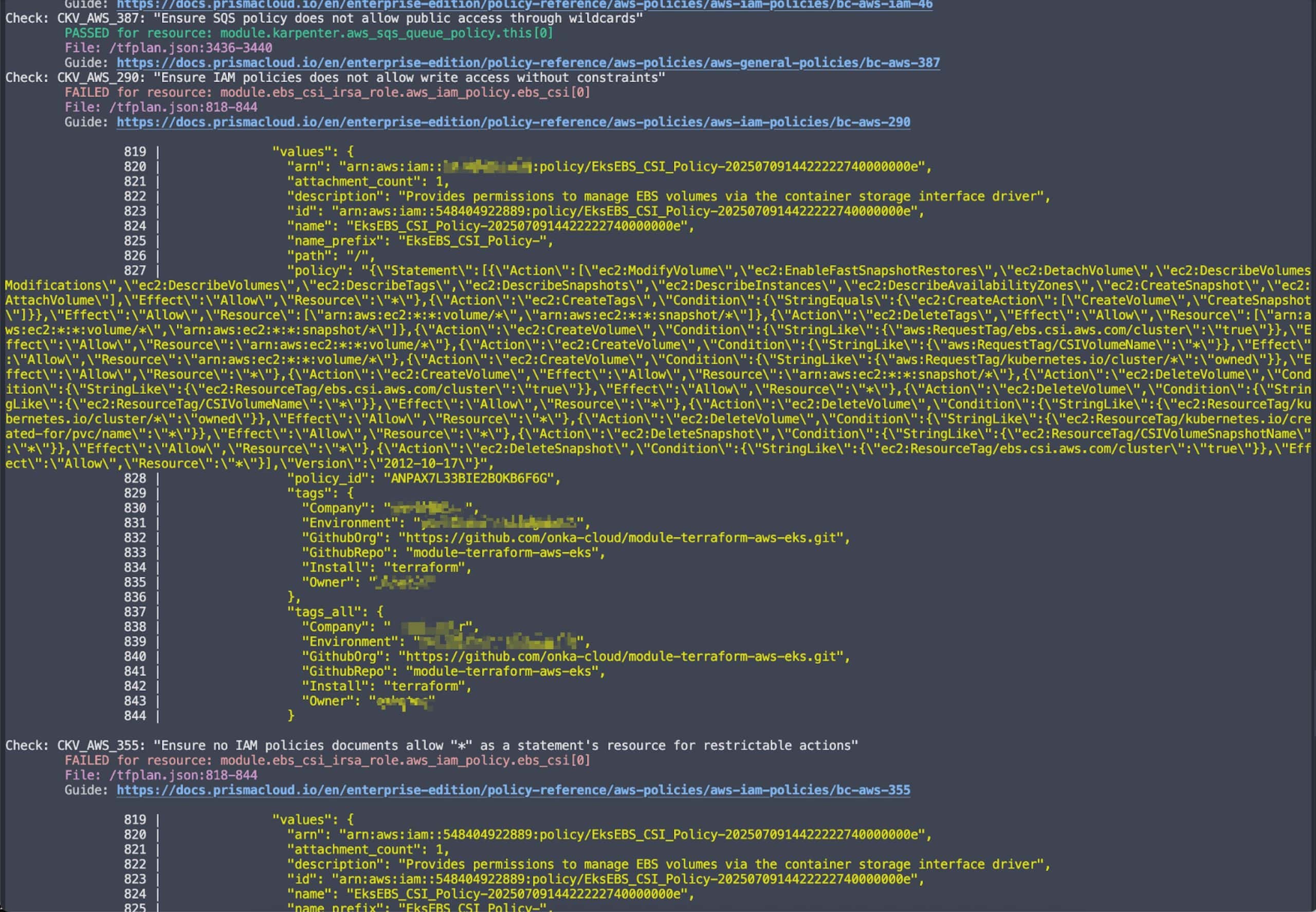
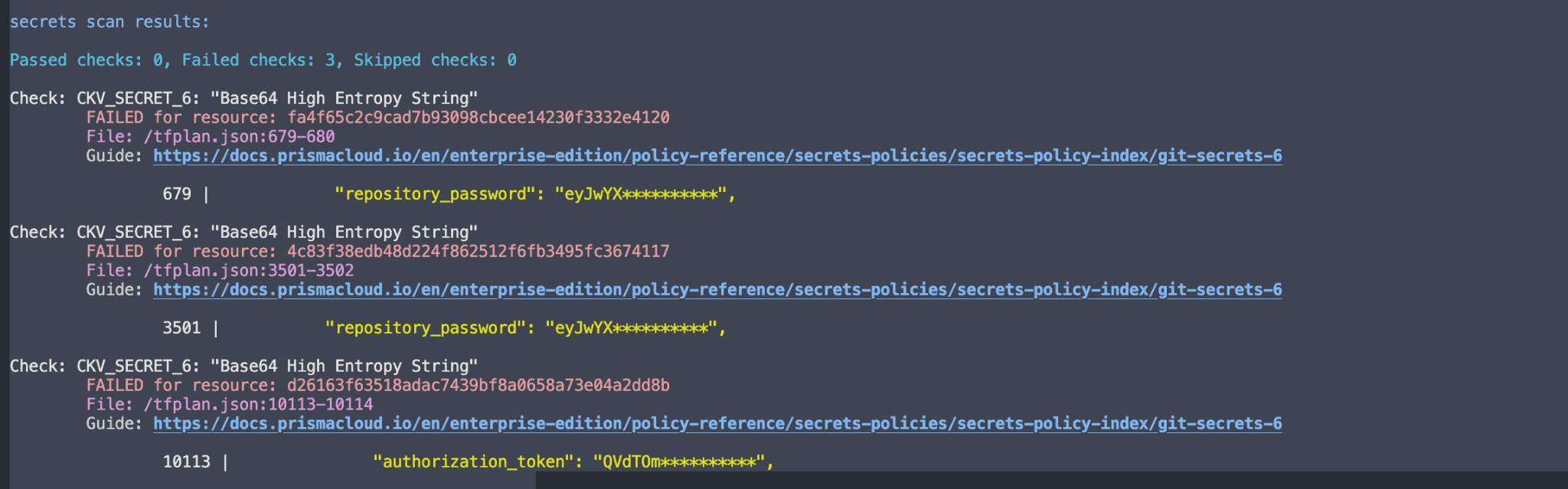
Komut çıktısı
[ kubernetes framework ]: 100%|████████████████████|[1/1], Current File Scanned=tfplan.json
[ secrets framework ]: 100%|████████████████████|[1/1], Current File Scanned=tfplan.jsonson
_ _
___| |__ ___ ___| | _______ __
/ __| '_ \ / _ \/ __| |/ / _ \ \ / /
| (__| | | | __/ (__| < (_) \ V /
\___|_| |_|\___|\___|_|\_\___/ \_/
By Prisma Cloud | version: 3.2.450
Update available 3.2.450 -> 3.2.461
Run pip3 install -U checkov to update
terraform_plan scan results:
Passed checks: 142, Failed checks: 9, Skipped checks: 0
Check: CKV_AWS_41: "Ensure no hard coded AWS access key and secret key exists in provider"
PASSED for resource: aws.default
File: /tfplan.json:19022-19039
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/secrets-policies/bc-aws-secrets-5
Check: CKV_AWS_41: "Ensure no hard coded AWS access key and secret key exists in provider"
PASSED for resource: aws.virginia
File: /tfplan.json:19039-19055
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/secrets-policies/bc-aws-secrets-5
Check: CKV_AWS_288: "Ensure IAM policies does not allow data exfiltration"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-288
Check: CKV_AWS_287: "Ensure IAM policies does not allow credentials exposure"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-287
Check: CKV_AWS_63: "Ensure no IAM policies documents allow "*" as a statement's actions"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/iam-48
Check: CKV_AWS_289: "Ensure IAM policies does not allow permissions management / resource exposure without constraints"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-289
Check: CKV_AWS_62: "Ensure IAM policies that allow full "*-*" administrative privileges are not created"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_286: "Ensure IAM policies does not allow privilege escalation"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-286
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_role.this[0]
File: /tfplan.json:858-891
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_61: "Ensure AWS IAM policy does not allow assume role permission across all services"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_role.this[0]
File: /tfplan.json:858-891
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_60: "Ensure IAM role allows only specific services or principals to assume it"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_role.this[0]
File: /tfplan.json:858-891
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-44
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.ebs_csi_irsa_role.aws_iam_role_policy_attachment.ebs_csi[0]
File: /tfplan.json:909-913
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_100: "Ensure AWS EKS node group does not have implicit SSH access from 0.0.0.0/0"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_eks_node_group.this[0]
File: /tfplan.json:2376-2451
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-kubernetes-policies/bc-aws-kubernetes-5
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role.this[0]
File: /tfplan.json:2492-2529
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_61: "Ensure AWS IAM policy does not allow assume role permission across all services"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role.this[0]
File: /tfplan.json:2492-2529
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_60: "Ensure IAM role allows only specific services or principals to assume it"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role.this[0]
File: /tfplan.json:2492-2529
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-44
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role_policy_attachment.additional["AWSLoadBalancerControllerIAMPolicy"]
File: /tfplan.json:2551-2555
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role_policy_attachment.additional["AmazonSSMManagedInstanceCore"]
File: /tfplan.json:2566-2570
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role_policy_attachment.this["AmazonEC2ContainerRegistryReadOnly"]
File: /tfplan.json:2581-2585
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role_policy_attachment.this["AmazonEKSWorkerNodePolicy"]
File: /tfplan.json:2596-2600
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.module.eks_managed_node_group["worker_general_t3a"].aws_iam_role_policy_attachment.this["AmazonEKS_CNI_Policy"]
File: /tfplan.json:2611-2615
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_227: "Ensure KMS key is enabled"
PASSED for resource: module.eks.module.kms.aws_kms_key.this[0]
File: /tfplan.json:2669-2692
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-general-policies/ensure-aws-key-management-service-kms-key-is-enabled
Check: CKV_AWS_33: "Ensure KMS key policy does not contain wildcard (*) principal"
PASSED for resource: module.eks.module.kms.aws_kms_key.this[0]
File: /tfplan.json:2669-2692
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/ensure-kms-key-policy-does-not-contain-wildcard-principal
Check: CKV_AWS_7: "Ensure rotation for customer created CMKs is enabled"
PASSED for resource: module.eks.module.kms.aws_kms_key.this[0]
File: /tfplan.json:2669-2692
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-logging-policies/logging-8
Check: CKV_AWS_66: "Ensure that CloudWatch Log Group specifies retention days"
PASSED for resource: module.eks.aws_cloudwatch_log_group.this[0]
File: /tfplan.json:929-944
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-logging-policies/logging-13
Check: CKV_AWS_39: "Ensure Amazon EKS public endpoint disabled"
PASSED for resource: module.eks.aws_eks_cluster.this[0]
File: /tfplan.json:1266-1368
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-kubernetes-policies/bc-aws-kubernetes-2
Check: CKV_AWS_58: "Ensure EKS Cluster has Secrets Encryption Enabled"
PASSED for resource: module.eks.aws_eks_cluster.this[0]
File: /tfplan.json:1266-1368
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-kubernetes-policies/bc-aws-kubernetes-3
Check: CKV_AWS_38: "Ensure Amazon EKS public endpoint not accessible to 0.0.0.0/0"
PASSED for resource: module.eks.aws_eks_cluster.this[0]
File: /tfplan.json:1266-1368
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-kubernetes-policies/bc-aws-kubernetes-1
Check: CKV_AWS_288: "Ensure IAM policies does not allow data exfiltration"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-288
Check: CKV_AWS_290: "Ensure IAM policies does not allow write access without constraints"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-290
Check: CKV_AWS_287: "Ensure IAM policies does not allow credentials exposure"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-287
Check: CKV_AWS_63: "Ensure no IAM policies documents allow "*" as a statement's actions"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/iam-48
Check: CKV_AWS_289: "Ensure IAM policies does not allow permissions management / resource exposure without constraints"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-289
Check: CKV_AWS_62: "Ensure IAM policies that allow full "*-*" administrative privileges are not created"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_355: "Ensure no IAM policies documents allow "*" as a statement's resource for restrictable actions"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-355
Check: CKV_AWS_286: "Ensure IAM policies does not allow privilege escalation"
PASSED for resource: module.eks.aws_iam_policy.cluster_encryption[0]
File: /tfplan.json:1477-1489
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-286
Check: CKV_AWS_288: "Ensure IAM policies does not allow data exfiltration"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-288
Check: CKV_AWS_290: "Ensure IAM policies does not allow write access without constraints"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-290
Check: CKV_AWS_287: "Ensure IAM policies does not allow credentials exposure"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-287
Check: CKV_AWS_63: "Ensure no IAM policies documents allow "*" as a statement's actions"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/iam-48
Check: CKV_AWS_289: "Ensure IAM policies does not allow permissions management / resource exposure without constraints"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-289
Check: CKV_AWS_62: "Ensure IAM policies that allow full "*-*" administrative privileges are not created"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_355: "Ensure no IAM policies documents allow "*" as a statement's resource for restrictable actions"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-355
Check: CKV_AWS_286: "Ensure IAM policies does not allow privilege escalation"
PASSED for resource: module.eks.aws_iam_policy.custom[0]
File: /tfplan.json:1503-1519
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-286
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role.this[0]
File: /tfplan.json:1533-1561
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_61: "Ensure AWS IAM policy does not allow assume role permission across all services"
PASSED for resource: module.eks.aws_iam_role.this[0]
File: /tfplan.json:1533-1561
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_60: "Ensure IAM role allows only specific services or principals to assume it"
PASSED for resource: module.eks.aws_iam_role.this[0]
File: /tfplan.json:1533-1561
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-44
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role_policy_attachment.additional["AWSLoadBalancerControllerIAMPolicy"]
File: /tfplan.json:1584-1588
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role_policy_attachment.additional["AmazonSSMManagedInstanceCore"]
File: /tfplan.json:1599-1603
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role_policy_attachment.cluster_encryption[0]
File: /tfplan.json:1614-1618
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role_policy_attachment.custom[0]
File: /tfplan.json:1629-1633
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role_policy_attachment.this["AmazonEKSClusterPolicy"]
File: /tfplan.json:1644-1648
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.eks.aws_iam_role_policy_attachment.this["AmazonEKSVPCResourceController"]
File: /tfplan.json:1659-1663
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group.cluster[0]
File: /tfplan.json:1674-1719
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group.cluster[0]
File: /tfplan.json:1674-1719
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group.cluster[0]
File: /tfplan.json:1674-1719
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group.cluster[0]
File: /tfplan.json:1674-1719
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group.cluster[0]
File: /tfplan.json:1674-1719
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_382: "Ensure no security groups allow egress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group.cluster[0]
File: /tfplan.json:1674-1719
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/bc-aws-382
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group.node[0]
File: /tfplan.json:1752-1912
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group.node[0]
File: /tfplan.json:1752-1912
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group.node[0]
File: /tfplan.json:1752-1912
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group.node[0]
File: /tfplan.json:1752-1912
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group.node[0]
File: /tfplan.json:1752-1912
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_nodes_443"]
File: /tfplan.json:2004-2019
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_nodes_443"]
File: /tfplan.json:2004-2019
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_nodes_443"]
File: /tfplan.json:2004-2019
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_nodes_443"]
File: /tfplan.json:2004-2019
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_nodes_443"]
File: /tfplan.json:2004-2019
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_source_security_group_id_vpn"]
File: /tfplan.json:2030-2047
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_source_security_group_id_vpn"]
File: /tfplan.json:2030-2047
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_source_security_group_id_vpn"]
File: /tfplan.json:2030-2047
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_source_security_group_id_vpn"]
File: /tfplan.json:2030-2047
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.cluster["ingress_source_security_group_id_vpn"]
File: /tfplan.json:2030-2047
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["egress_all"]
File: /tfplan.json:2062-2079
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_443"]
File: /tfplan.json:2095-2110
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_443"]
File: /tfplan.json:2095-2110
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_443"]
File: /tfplan.json:2095-2110
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_443"]
File: /tfplan.json:2095-2110
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_443"]
File: /tfplan.json:2095-2110
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_4443_webhook"]
File: /tfplan.json:2123-2138
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_4443_webhook"]
File: /tfplan.json:2123-2138
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_4443_webhook"]
File: /tfplan.json:2123-2138
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_4443_webhook"]
File: /tfplan.json:2123-2138
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_4443_webhook"]
File: /tfplan.json:2123-2138
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_6443_webhook"]
File: /tfplan.json:2151-2166
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_6443_webhook"]
File: /tfplan.json:2151-2166
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_6443_webhook"]
File: /tfplan.json:2151-2166
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_6443_webhook"]
File: /tfplan.json:2151-2166
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_6443_webhook"]
File: /tfplan.json:2151-2166
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_8443_webhook"]
File: /tfplan.json:2179-2194
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_8443_webhook"]
File: /tfplan.json:2179-2194
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_8443_webhook"]
File: /tfplan.json:2179-2194
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_8443_webhook"]
File: /tfplan.json:2179-2194
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_8443_webhook"]
File: /tfplan.json:2179-2194
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_9443_webhook"]
File: /tfplan.json:2207-2222
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_9443_webhook"]
File: /tfplan.json:2207-2222
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_9443_webhook"]
File: /tfplan.json:2207-2222
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_9443_webhook"]
File: /tfplan.json:2207-2222
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_9443_webhook"]
File: /tfplan.json:2207-2222
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_kubelet"]
File: /tfplan.json:2235-2250
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_kubelet"]
File: /tfplan.json:2235-2250
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_kubelet"]
File: /tfplan.json:2235-2250
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_kubelet"]
File: /tfplan.json:2235-2250
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_cluster_kubelet"]
File: /tfplan.json:2235-2250
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_nodes_ephemeral"]
File: /tfplan.json:2263-2278
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_nodes_ephemeral"]
File: /tfplan.json:2263-2278
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_nodes_ephemeral"]
File: /tfplan.json:2263-2278
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_nodes_ephemeral"]
File: /tfplan.json:2263-2278
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_nodes_ephemeral"]
File: /tfplan.json:2263-2278
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_tcp"]
File: /tfplan.json:2291-2306
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_tcp"]
File: /tfplan.json:2291-2306
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_tcp"]
File: /tfplan.json:2291-2306
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_tcp"]
File: /tfplan.json:2291-2306
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_tcp"]
File: /tfplan.json:2291-2306
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_260: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 80"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_udp"]
File: /tfplan.json:2319-2334
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-groups-do-not-allow-ingress-from-00000-to-port-80
Check: CKV_AWS_24: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 22"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_udp"]
File: /tfplan.json:2319-2334
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-1-port-security
Check: CKV_AWS_23: "Ensure every security group and rule has a description"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_udp"]
File: /tfplan.json:2319-2334
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-31
Check: CKV_AWS_277: "Ensure no security groups allow ingress from 0.0.0.0:0 to port -1"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_udp"]
File: /tfplan.json:2319-2334
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/ensure-aws-security-group-does-not-allow-all-traffic-on-all-ports
Check: CKV_AWS_25: "Ensure no security groups allow ingress from 0.0.0.0:0 to port 3389"
PASSED for resource: module.eks.aws_security_group_rule.node["ingress_self_coredns_udp"]
File: /tfplan.json:2319-2334
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/networking-2
Check: CKV_AWS_288: "Ensure IAM policies does not allow data exfiltration"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-288
Check: CKV_AWS_290: "Ensure IAM policies does not allow write access without constraints"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-290
Check: CKV_AWS_287: "Ensure IAM policies does not allow credentials exposure"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-287
Check: CKV_AWS_63: "Ensure no IAM policies documents allow "*" as a statement's actions"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/iam-48
Check: CKV_AWS_289: "Ensure IAM policies does not allow permissions management / resource exposure without constraints"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-289
Check: CKV_AWS_62: "Ensure IAM policies that allow full "*-*" administrative privileges are not created"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_286: "Ensure IAM policies does not allow privilege escalation"
PASSED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-286
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role.controller[0]
File: /tfplan.json:3201-3234
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_61: "Ensure AWS IAM policy does not allow assume role permission across all services"
PASSED for resource: module.karpenter.aws_iam_role.controller[0]
File: /tfplan.json:3201-3234
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_60: "Ensure IAM role allows only specific services or principals to assume it"
PASSED for resource: module.karpenter.aws_iam_role.controller[0]
File: /tfplan.json:3201-3234
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-44
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role.node[0]
File: /tfplan.json:3252-3288
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_61: "Ensure AWS IAM policy does not allow assume role permission across all services"
PASSED for resource: module.karpenter.aws_iam_role.node[0]
File: /tfplan.json:3252-3288
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-45
Check: CKV_AWS_60: "Ensure IAM role allows only specific services or principals to assume it"
PASSED for resource: module.karpenter.aws_iam_role.node[0]
File: /tfplan.json:3252-3288
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-44
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role_policy_attachment.controller[0]
File: /tfplan.json:3309-3313
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role_policy_attachment.node["AmazonEC2ContainerRegistryReadOnly"]
File: /tfplan.json:3324-3328
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role_policy_attachment.node["AmazonEKSWorkerNodePolicy"]
File: /tfplan.json:3339-3343
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role_policy_attachment.node["AmazonEKS_CNI_Policy"]
File: /tfplan.json:3354-3358
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_274: "Disallow IAM roles, users, and groups from using the AWS AdministratorAccess policy"
PASSED for resource: module.karpenter.aws_iam_role_policy_attachment.node_additional["AmazonSSMManagedInstanceCore"]
File: /tfplan.json:3369-3373
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-274
Check: CKV_AWS_27: "Ensure all data stored in the SQS queue is encrypted"
PASSED for resource: module.karpenter.aws_sqs_queue.this[0]
File: /tfplan.json:3384-3422
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-general-policies/general-16-encrypt-sqs-queue
Check: CKV_AWS_168: "Ensure SQS queue policy is not public by only allowing specific services or principals to access it"
PASSED for resource: module.karpenter.aws_sqs_queue_policy.this[0]
File: /tfplan.json:3436-3440
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-general-policies/ensure-sqs-queue-policy-is-not-public-by-only-allowing-specific-services-or-principals-to-access-it
Check: CKV_AWS_72: "Ensure SQS policy does not allow ALL (*) actions."
PASSED for resource: module.karpenter.aws_sqs_queue_policy.this[0]
File: /tfplan.json:3436-3440
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-iam-46
Check: CKV_AWS_387: "Ensure SQS policy does not allow public access through wildcards"
PASSED for resource: module.karpenter.aws_sqs_queue_policy.this[0]
File: /tfplan.json:3436-3440
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-general-policies/bc-aws-387
Check: CKV_AWS_290: "Ensure IAM policies does not allow write access without constraints"
FAILED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-290
819 | "values": {
820 | "arn": "arn:aws:iam::548404922889:policy/EksEBS_CSI_Policy-2025070914422222740000000e",
821 | "attachment_count": 1,
822 | "description": "Provides permissions to manage EBS volumes via the container storage interface driver",
823 | "id": "arn:aws:iam::548404922889:policy/EksEBS_CSI_Policy-2025070914422222740000000e",
824 | "name": "EksEBS_CSI_Policy-2025070914422222740000000e",
825 | "name_prefix": "EksEBS_CSI_Policy-",
826 | "path": "/",
827 | "policy": "{\"Statement\":[{\"Action\":[\"ec2:ModifyVolume\",\"ec2:EnableFastSnapshotRestores\",\"ec2:DetachVolume\",\"ec2:DescribeVolumesModifications\",\"ec2:DescribeVolumes\",\"ec2:DescribeTags\",\"ec2:DescribeSnapshots\",\"ec2:DescribeInstances\",\"ec2:DescribeAvailabilityZones\",\"ec2:CreateSnapshot\",\"ec2:AttachVolume\"],\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:CreateTags\",\"Condition\":{\"StringEquals\":{\"ec2:CreateAction\":[\"CreateVolume\",\"CreateSnapshot\"]}},\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:volume/*\",\"arn:aws:ec2:*:*:snapshot/*\"]},{\"Action\":\"ec2:DeleteTags\",\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:volume/*\",\"arn:aws:ec2:*:*:snapshot/*\"]},{\"Action\":\"ec2:CreateVolume\",\"Condition\":{\"StringLike\":{\"aws:RequestTag/ebs.csi.aws.com/cluster\":\"true\"}},\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:volume/*\"},{\"Action\":\"ec2:CreateVolume\",\"Condition\":{\"StringLike\":{\"aws:RequestTag/CSIVolumeName\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:volume/*\"},{\"Action\":\"ec2:CreateVolume\",\"Condition\":{\"StringLike\":{\"aws:RequestTag/kubernetes.io/cluster/*\":\"owned\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:CreateVolume\",\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:snapshot/*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/ebs.csi.aws.com/cluster\":\"true\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/CSIVolumeName\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/kubernetes.io/cluster/*\":\"owned\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/kubernetes.io/created-for/pvc/name\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteSnapshot\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/CSIVolumeSnapshotName\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteSnapshot\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/ebs.csi.aws.com/cluster\":\"true\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"}],\"Version\":\"2012-10-17\"}",
828 | "policy_id": "ANPAX7L33BIE2BOKB6F6G",
829 | "tags": {
830 | "Company": "Test",
831 | "Environment": "Test-management",
832 | "GithubOrg": "https://github.com/onka-cloud/module-terraform-aws-eks.git",
833 | "GithubRepo": "module-terraform-aws-eks",
834 | "Install": "terraform",
835 | "Owner": "serdar"
836 | },
837 | "tags_all": {
838 | "Company": "Test",
839 | "Environment": "Test-management",
840 | "GithubOrg": "https://github.com/onka-cloud/module-terraform-aws-eks.git",
841 | "GithubRepo": "module-terraform-aws-eks",
842 | "Install": "terraform",
843 | "Owner": "serdar"
844 | }
Check: CKV_AWS_355: "Ensure no IAM policies documents allow "*" as a statement's resource for restrictable actions"
FAILED for resource: module.ebs_csi_irsa_role.aws_iam_policy.ebs_csi[0]
File: /tfplan.json:818-844
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-355
819 | "values": {
820 | "arn": "arn:aws:iam::548404922889:policy/EksEBS_CSI_Policy-2025070914422222740000000e",
821 | "attachment_count": 1,
822 | "description": "Provides permissions to manage EBS volumes via the container storage interface driver",
823 | "id": "arn:aws:iam::548404922889:policy/EksEBS_CSI_Policy-2025070914422222740000000e",
824 | "name": "EksEBS_CSI_Policy-2025070914422222740000000e",
825 | "name_prefix": "EksEBS_CSI_Policy-",
826 | "path": "/",
827 | "policy": "{\"Statement\":[{\"Action\":[\"ec2:ModifyVolume\",\"ec2:EnableFastSnapshotRestores\",\"ec2:DetachVolume\",\"ec2:DescribeVolumesModifications\",\"ec2:DescribeVolumes\",\"ec2:DescribeTags\",\"ec2:DescribeSnapshots\",\"ec2:DescribeInstances\",\"ec2:DescribeAvailabilityZones\",\"ec2:CreateSnapshot\",\"ec2:AttachVolume\"],\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:CreateTags\",\"Condition\":{\"StringEquals\":{\"ec2:CreateAction\":[\"CreateVolume\",\"CreateSnapshot\"]}},\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:volume/*\",\"arn:aws:ec2:*:*:snapshot/*\"]},{\"Action\":\"ec2:DeleteTags\",\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:volume/*\",\"arn:aws:ec2:*:*:snapshot/*\"]},{\"Action\":\"ec2:CreateVolume\",\"Condition\":{\"StringLike\":{\"aws:RequestTag/ebs.csi.aws.com/cluster\":\"true\"}},\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:volume/*\"},{\"Action\":\"ec2:CreateVolume\",\"Condition\":{\"StringLike\":{\"aws:RequestTag/CSIVolumeName\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:volume/*\"},{\"Action\":\"ec2:CreateVolume\",\"Condition\":{\"StringLike\":{\"aws:RequestTag/kubernetes.io/cluster/*\":\"owned\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:CreateVolume\",\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:snapshot/*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/ebs.csi.aws.com/cluster\":\"true\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/CSIVolumeName\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/kubernetes.io/cluster/*\":\"owned\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteVolume\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/kubernetes.io/created-for/pvc/name\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteSnapshot\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/CSIVolumeSnapshotName\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"},{\"Action\":\"ec2:DeleteSnapshot\",\"Condition\":{\"StringLike\":{\"ec2:ResourceTag/ebs.csi.aws.com/cluster\":\"true\"}},\"Effect\":\"Allow\",\"Resource\":\"*\"}],\"Version\":\"2012-10-17\"}",
828 | "policy_id": "ANPAX7L33BIE2BOKB6F6G",
829 | "tags": {
830 | "Company": "Test",
831 | "Environment": "Test-management",
832 | "GithubOrg": "https://github.com/onka-cloud/module-terraform-aws-eks.git",
833 | "GithubRepo": "module-terraform-aws-eks",
834 | "Install": "terraform",
835 | "Owner": "serdar"
836 | },
837 | "tags_all": {
838 | "Company": "Test",
839 | "Environment": "Test-management",
840 | "GithubOrg": "https://github.com/onka-cloud/module-terraform-aws-eks.git",
841 | "GithubRepo": "module-terraform-aws-eks",
842 | "Install": "terraform",
843 | "Owner": "serdar"
844 | }
Check: CKV_AWS_338: "Ensure CloudWatch log groups retains logs for at least 1 year"
FAILED for resource: module.eks.aws_cloudwatch_log_group.this[0]
File: /tfplan.json:929-944
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-logging-policies/bc-aws-338
930 | "values": {
931 | "arn": "arn:aws:logs:eu-central-1:548404922889:log-group:/aws/eks/Test-management-eks/cluster",
932 | "id": "/aws/eks/Test-management-eks/cluster",
933 | "kms_key_id": "",
934 | "log_group_class": "STANDARD",
935 | "name": "/aws/eks/Test-management-eks/cluster",
936 | "name_prefix": "",
937 | "retention_in_days": 90,
938 | "skip_destroy": false,
939 | "tags": {
940 | "Name": "/aws/eks/Test-management-eks/cluster"
941 | },
942 | "tags_all": {
943 | "Name": "/aws/eks/Test-management-eks/cluster"
944 | }
Check: CKV_AWS_158: "Ensure that CloudWatch Log Group is encrypted by KMS"
FAILED for resource: module.eks.aws_cloudwatch_log_group.this[0]
File: /tfplan.json:929-944
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-general-policies/ensure-that-cloudwatch-log-group-is-encrypted-by-kms
930 | "values": {
931 | "arn": "arn:aws:logs:eu-central-1:548404922889:log-group:/aws/eks/Test-management-eks/cluster",
932 | "id": "/aws/eks/Test-management-eks/cluster",
933 | "kms_key_id": "",
934 | "log_group_class": "STANDARD",
935 | "name": "/aws/eks/Test-management-eks/cluster",
936 | "name_prefix": "",
937 | "retention_in_days": 90,
938 | "skip_destroy": false,
939 | "tags": {
940 | "Name": "/aws/eks/Test-management-eks/cluster"
941 | },
942 | "tags_all": {
943 | "Name": "/aws/eks/Test-management-eks/cluster"
944 | }
Check: CKV_AWS_339: "Ensure EKS clusters run on a supported Kubernetes version"
FAILED for resource: module.eks.aws_eks_cluster.this[0]
File: /tfplan.json:1266-1368
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-kubernetes-policies/bc-aws-339
Code lines for this resource are too many. Please use IDE of your choice to review the file.
Check: CKV_AWS_37: "Ensure Amazon EKS control plane logging is enabled for all log types"
FAILED for resource: module.eks.aws_eks_cluster.this[0]
File: /tfplan.json:1266-1368
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-kubernetes-policies/bc-aws-kubernetes-4
Code lines for this resource are too many. Please use IDE of your choice to review the file.
Check: CKV_AWS_382: "Ensure no security groups allow egress from 0.0.0.0:0 to port -1"
FAILED for resource: module.eks.aws_security_group.node[0]
File: /tfplan.json:1752-1912
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/bc-aws-382
Code lines for this resource are too many. Please use IDE of your choice to review the file.
Check: CKV_AWS_382: "Ensure no security groups allow egress from 0.0.0.0:0 to port -1"
FAILED for resource: module.eks.aws_security_group_rule.node["egress_all"]
File: /tfplan.json:2062-2079
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-networking-policies/bc-aws-382
2063 | "values": {
2064 | "cidr_blocks": [
2065 | "0.0.0.0/0"
2066 | ],
2067 | "description": "Allow all egress",
2068 | "from_port": 0,
2069 | "id": "sgrule-3572562169",
2070 | "ipv6_cidr_blocks": null,
2071 | "prefix_list_ids": [],
2072 | "protocol": "-1",
2073 | "security_group_id": "sg-0760ef601429274fe",
2074 | "security_group_rule_id": "sgr-0fe8e6f0f81469e6b",
2075 | "self": false,
2076 | "source_security_group_id": null,
2077 | "timeouts": null,
2078 | "to_port": 0,
2079 | "type": "egress"
Check: CKV_AWS_355: "Ensure no IAM policies documents allow "*" as a statement's resource for restrictable actions"
FAILED for resource: module.karpenter.aws_iam_policy.controller[0]
File: /tfplan.json:3161-3187
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/aws-policies/aws-iam-policies/bc-aws-355
3162 | "values": {
3163 | "arn": "arn:aws:iam::548404922889:policy/KarpenterController-2025070914411110290000000c",
3164 | "attachment_count": 1,
3165 | "description": "Karpenter controller IAM policy",
3166 | "id": "arn:aws:iam::548404922889:policy/KarpenterController-2025070914411110290000000c",
3167 | "name": "KarpenterController-2025070914411110290000000c",
3168 | "name_prefix": "KarpenterController-",
3169 | "path": "/",
3170 | "policy": "{\"Statement\":[{\"Action\":[\"ec2:RunInstances\",\"ec2:CreateFleet\"],\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*::snapshot/*\",\"arn:aws:ec2:*::image/*\",\"arn:aws:ec2:*:*:subnet/*\",\"arn:aws:ec2:*:*:spot-instances-request/*\",\"arn:aws:ec2:*:*:security-group/*\",\"arn:aws:ec2:*:*:launch-template/*\"],\"Sid\":\"AllowScopedEC2InstanceActions\"},{\"Action\":[\"ec2:RunInstances\",\"ec2:CreateLaunchTemplate\",\"ec2:CreateFleet\"],\"Condition\":{\"StringEquals\":{\"aws:RequestTag/kubernetes.io/cluster/Test-management-eks\":\"owned\"},\"StringLike\":{\"aws:RequestTag/karpenter.sh/nodepool\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:volume/*\",\"arn:aws:ec2:*:*:spot-instances-request/*\",\"arn:aws:ec2:*:*:network-interface/*\",\"arn:aws:ec2:*:*:launch-template/*\",\"arn:aws:ec2:*:*:instance/*\",\"arn:aws:ec2:*:*:fleet/*\"],\"Sid\":\"AllowScopedEC2InstanceActionsWithTags\"},{\"Action\":\"ec2:CreateTags\",\"Condition\":{\"StringEquals\":{\"aws:RequestTag/kubernetes.io/cluster/Test-management-eks\":\"owned\",\"ec2:CreateAction\":[\"RunInstances\",\"CreateFleet\",\"CreateLaunchTemplate\"]},\"StringLike\":{\"aws:RequestTag/karpenter.sh/nodepool\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:volume/*\",\"arn:aws:ec2:*:*:spot-instances-request/*\",\"arn:aws:ec2:*:*:network-interface/*\",\"arn:aws:ec2:*:*:launch-template/*\",\"arn:aws:ec2:*:*:instance/*\",\"arn:aws:ec2:*:*:fleet/*\"],\"Sid\":\"AllowScopedResourceCreationTagging\"},{\"Action\":\"ec2:CreateTags\",\"Condition\":{\"ForAllValues:StringEquals\":{\"aws:TagKeys\":[\"karpenter.sh/nodeclaim\",\"Name\"]},\"StringEquals\":{\"aws:ResourceTag/kubernetes.io/cluster/Test-management-eks\":\"owned\"},\"StringLike\":{\"aws:ResourceTag/karpenter.sh/nodepool\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ec2:*:*:instance/*\",\"Sid\":\"AllowScopedResourceTagging\"},{\"Action\":[\"ec2:TerminateInstances\",\"ec2:DeleteLaunchTemplate\"],\"Condition\":{\"StringEquals\":{\"aws:ResourceTag/kubernetes.io/cluster/Test-management-eks\":\"owned\"},\"StringLike\":{\"aws:ResourceTag/karpenter.sh/nodepool\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":[\"arn:aws:ec2:*:*:launch-template/*\",\"arn:aws:ec2:*:*:instance/*\"],\"Sid\":\"AllowScopedDeletion\"},{\"Action\":[\"ec2:DescribeSubnets\",\"ec2:DescribeSpotPriceHistory\",\"ec2:DescribeSecurityGroups\",\"ec2:DescribeLaunchTemplates\",\"ec2:DescribeInstances\",\"ec2:DescribeInstanceTypes\",\"ec2:DescribeInstanceTypeOfferings\",\"ec2:DescribeImages\",\"ec2:DescribeAvailabilityZones\"],\"Condition\":{\"StringEquals\":{\"aws:RequestedRegion\":\"eu-central-1\"}},\"Effect\":\"Allow\",\"Resource\":\"*\",\"Sid\":\"AllowRegionalReadActions\"},{\"Action\":\"ssm:GetParameter\",\"Effect\":\"Allow\",\"Resource\":\"arn:aws:ssm:eu-central-1::parameter/aws/service/*\",\"Sid\":\"AllowSSMReadActions\"},{\"Action\":\"pricing:GetProducts\",\"Effect\":\"Allow\",\"Resource\":\"*\",\"Sid\":\"AllowPricingReadActions\"},{\"Action\":[\"sqs:ReceiveMessage\",\"sqs:GetQueueUrl\",\"sqs:GetQueueAttributes\",\"sqs:DeleteMessage\"],\"Effect\":\"Allow\",\"Resource\":\"arn:aws:sqs:eu-central-1:548404922889:Karpenter-Test-management-eks\",\"Sid\":\"AllowInterruptionQueueActions\"},{\"Action\":\"iam:PassRole\",\"Condition\":{\"StringEquals\":{\"iam:PassedToService\":\"ec2.amazonaws.com\"}},\"Effect\":\"Allow\",\"Resource\":\"arn:aws:iam::548404922889:role/Karpenter-Test-management-eks-20250709144044563100000006\",\"Sid\":\"AllowPassingInstanceRole\"},{\"Action\":\"iam:CreateInstanceProfile\",\"Condition\":{\"StringEquals\":{\"aws:RequestTag/kubernetes.io/cluster/Test-management-eks\":\"owned\",\"aws:RequestTag/topology.kubernetes.io/region\":\"eu-central-1\"},\"StringLike\":{\"aws:RequestTag/karpenter.k8s.aws/ec2nodeclass\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\",\"Sid\":\"AllowScopedInstanceProfileCreationActions\"},{\"Action\":\"iam:TagInstanceProfile\",\"Condition\":{\"StringEquals\":{\"aws:RequestTag/kubernetes.io/cluster/Test-management-eks\":\"owned\",\"aws:ResourceTag/kubernetes.io/cluster/Test-management-eks\":\"owned\",\"aws:ResourceTag/topology.kubernetes.io/region\":\"eu-central-1\"},\"StringLike\":{\"aws:RequestTag/karpenter.k8s.aws/ec2nodeclass\":\"*\",\"aws:ResourceTag/karpenter.k8s.aws/ec2nodeclass\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\",\"Sid\":\"AllowScopedInstanceProfileTagActions\"},{\"Action\":[\"iam:RemoveRoleFromInstanceProfile\",\"iam:DeleteInstanceProfile\",\"iam:AddRoleToInstanceProfile\"],\"Condition\":{\"StringEquals\":{\"aws:ResourceTag/kubernetes.io/cluster/Test-management-eks\":\"owned\",\"aws:ResourceTag/topology.kubernetes.io/region\":\"eu-central-1\"},\"StringLike\":{\"aws:ResourceTag/karpenter.k8s.aws/ec2nodeclass\":\"*\"}},\"Effect\":\"Allow\",\"Resource\":\"*\",\"Sid\":\"AllowScopedInstanceProfileActions\"},{\"Action\":\"iam:GetInstanceProfile\",\"Effect\":\"Allow\",\"Resource\":\"*\",\"Sid\":\"AllowInstanceProfileReadActions\"},{\"Action\":\"eks:DescribeCluster\",\"Effect\":\"Allow\",\"Resource\":\"arn:aws:eks:eu-central-1:548404922889:cluster/Test-management-eks\",\"Sid\":\"AllowAPIServerEndpointDiscovery\"}],\"Version\":\"2012-10-17\"}",
3171 | "policy_id": "ANPAX7L33BIETLVCYQYGU",
3172 | "tags": {
3173 | "Company": "Test",
3174 | "Environment": "Test-management",
3175 | "GithubOrg": "https://github.com/onka-cloud/module-terraform-aws-eks.git",
3176 | "GithubRepo": "module-terraform-aws-eks",
3177 | "Install": "terraform",
3178 | "Owner": "serdar"
3179 | },
3180 | "tags_all": {
3181 | "Company": "Test",
3182 | "Environment": "Test-management",
3183 | "GithubOrg": "https://github.com/onka-cloud/module-terraform-aws-eks.git",
3184 | "GithubRepo": "module-terraform-aws-eks",
3185 | "Install": "terraform",
3186 | "Owner": "serdar"
3187 | }
secrets scan results:
Passed checks: 0, Failed checks: 3, Skipped checks: 0
Check: CKV_SECRET_6: "Base64 High Entropy String"
FAILED for resource: fa4f65c2c9cad7b93098cbcee14230f3332e4120
File: /tfplan.json:679-680
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/secrets-policies/secrets-policy-index/git-secrets-6
679 | "repository_password": "eyJwYX**********",
Check: CKV_SECRET_6: "Base64 High Entropy String"
FAILED for resource: 4c83f38edb48d224f862512f6fb3495fc3674117
File: /tfplan.json:3501-3502
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/secrets-policies/secrets-policy-index/git-secrets-6
3501 | "repository_password": "eyJwYX**********",
Check: CKV_SECRET_6: "Base64 High Entropy String"
FAILED for resource: d26163f63518adac7439bf8a0658a73e04a2dd8b
File: /tfplan.json:10113-10114
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/secrets-policies/secrets-policy-index/git-secrets-6
10113 | "authorization_token": "QVdTOm**********",




