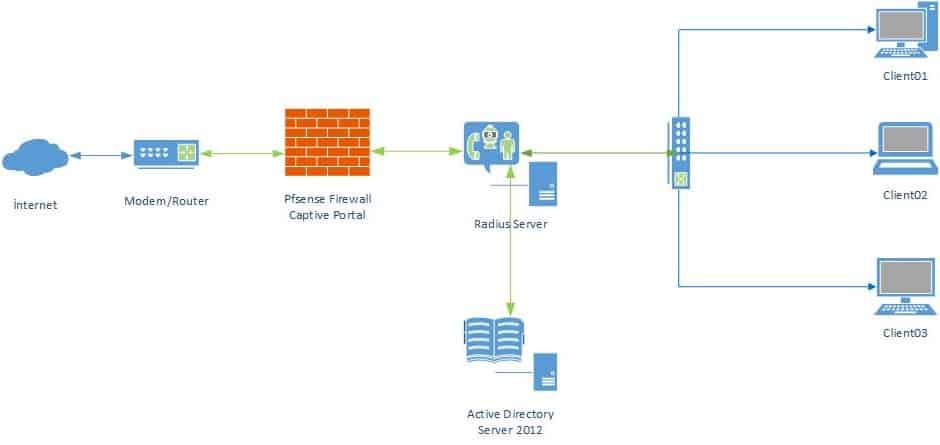
Pfsense Captive portal MSRadius AD Authentication


Hi friends MS Radius server with our present-day issues on the portal Captive pfSense acted in active directory user or group will provide a web output power.
What we’re going operations;
- PfSense Captive Portal configuration
- Radius Server 2012 on the server installation and configuration
- Captive portal Radius Server integration.
The scheme will be made as follows of friends here.
First we build our RADIUS server, I use my machine for the ADR process only 2 Role in the machine …
Server 2012 Radius Server Installation
1-)
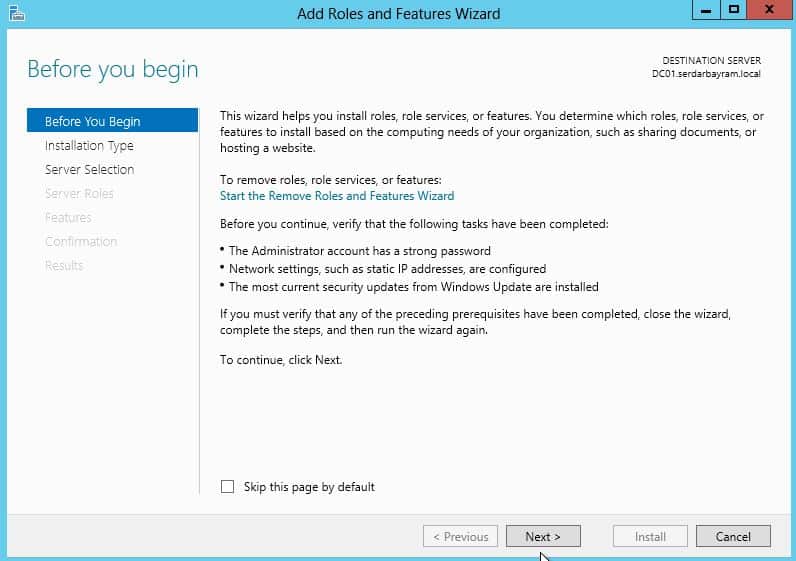
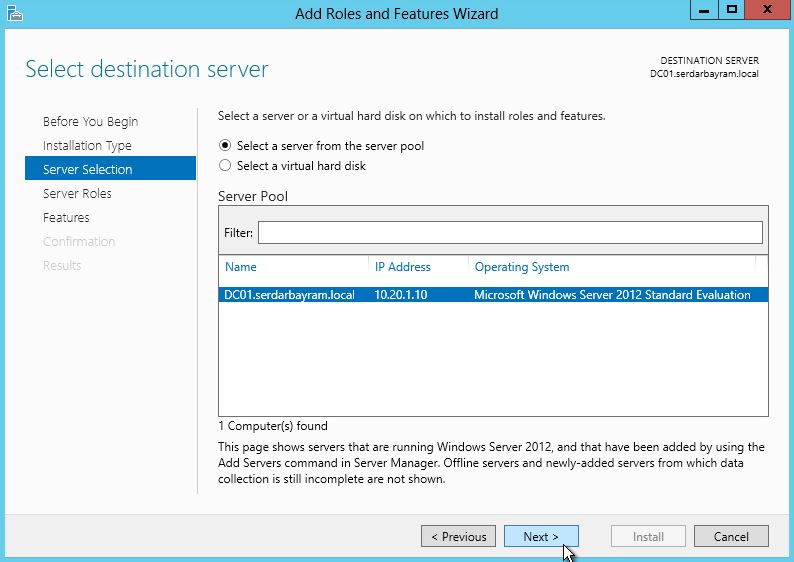
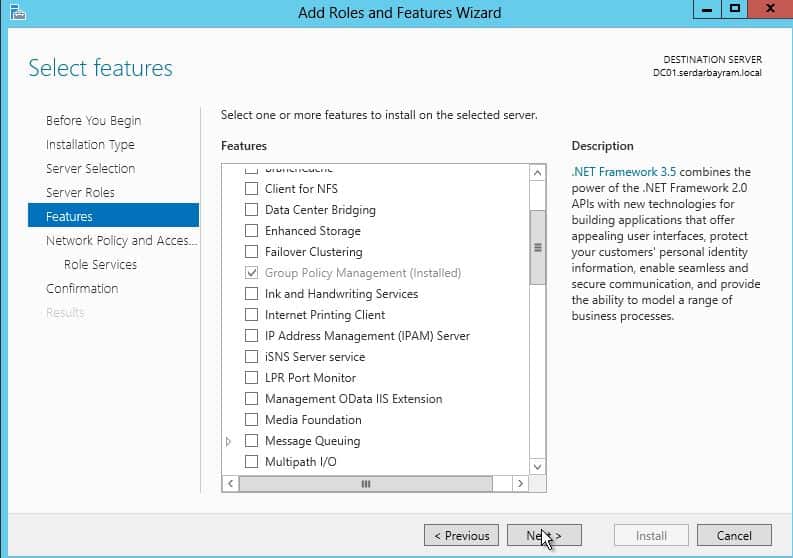
First we choose the Add Roles and ftur u our screen server manager.

Select the Network Policy and Access Services option we load our sever the Radius server service.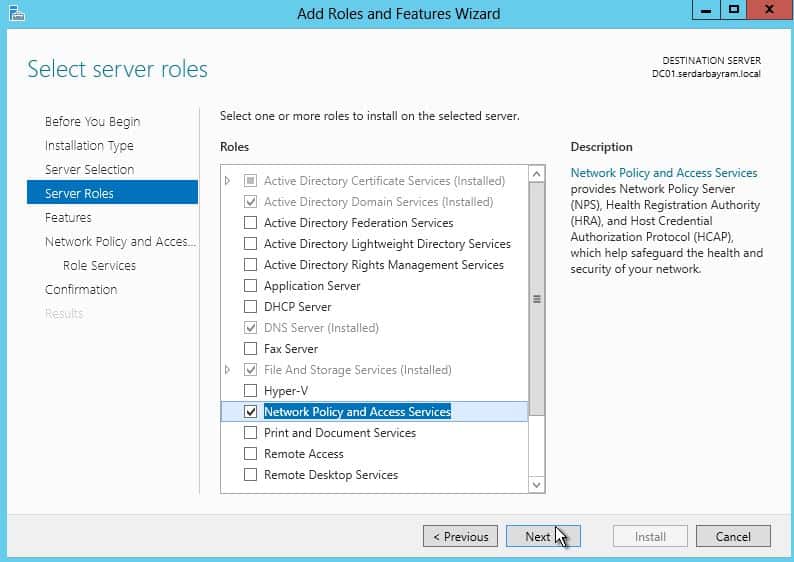

Install complete your installation saying.
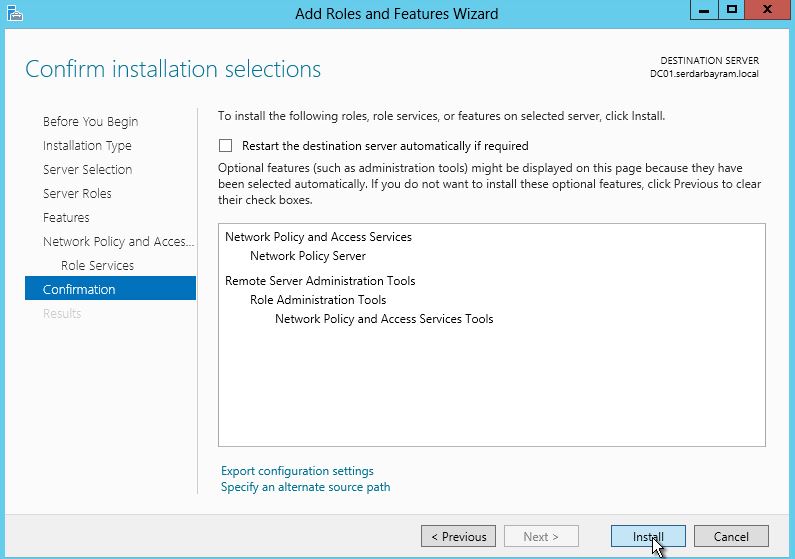
Yes, now we will be ready to configure RADIUS server.
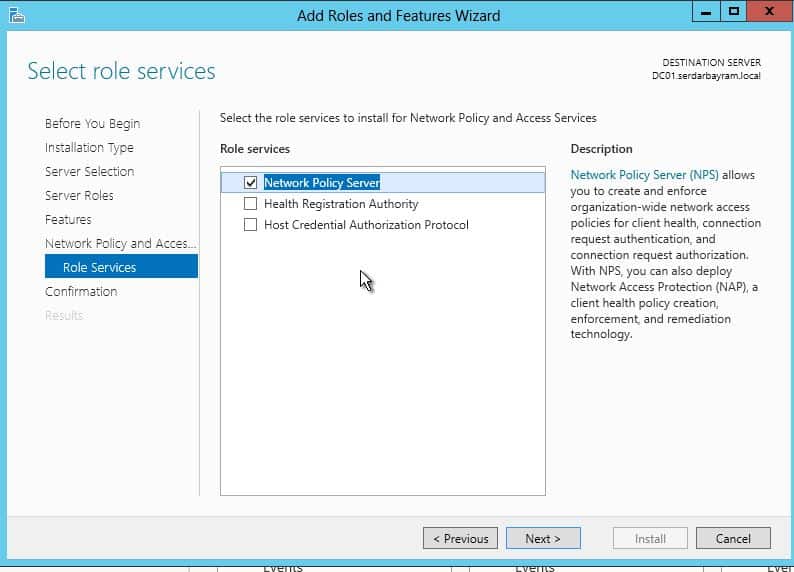
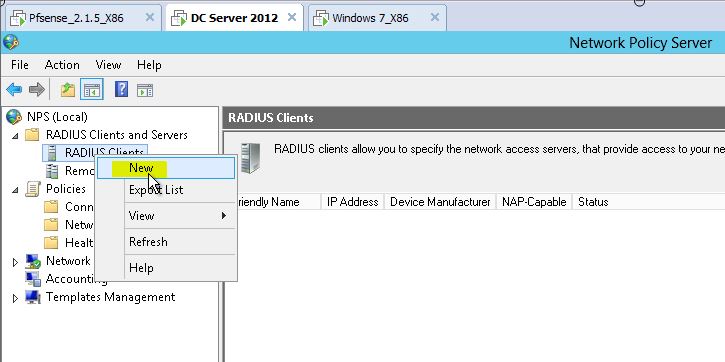
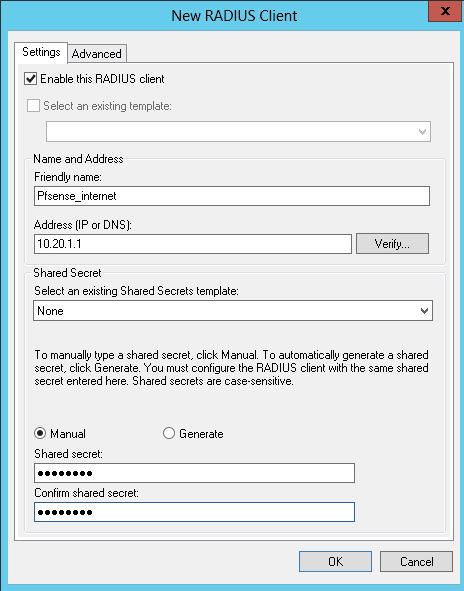
2-) Radius Client a right click on them first and then we configure our Radius client.
Here I give a name for the Radius Client (this name is important because the zone name will create a captive portal on pfSense have to be the same) Address section I’m going to pfSense machine’s IP address.
In the lower section I set a security password and record saying I’m OK.
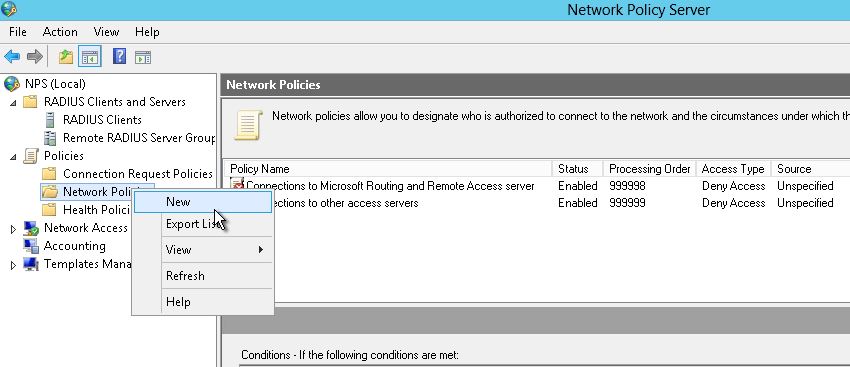
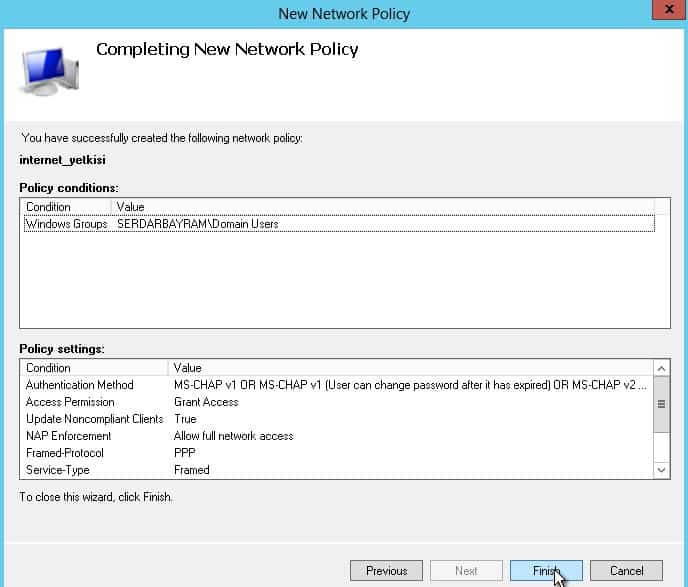
3-) Polices –>We come to the department and we are creating a new network rule saying.
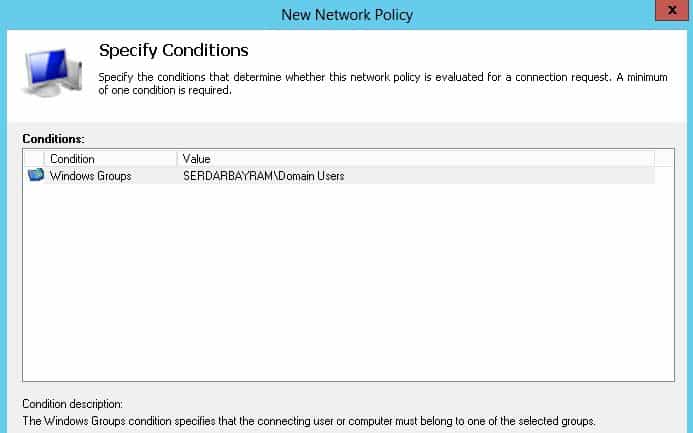
We continue to give a name to our Rule.

I choose the place add diyer will make the Radius server authentication On this page I want here Active directory in which all domain users with the emergence of the internet, but you know authorize selecting here in any group you specify.

Our rule will permit a transition rule “Access Granted” We continue with the option.

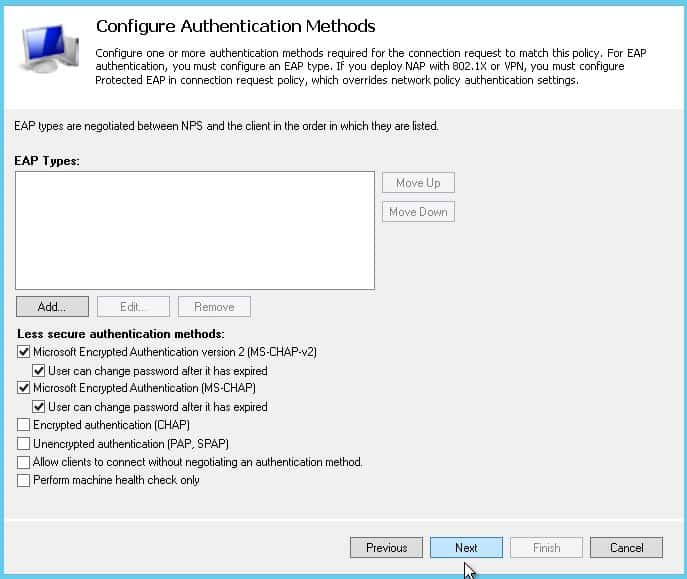

Encryption section of “No encryption” We remove the check mark from the box.

Finish saying we complete our rule.
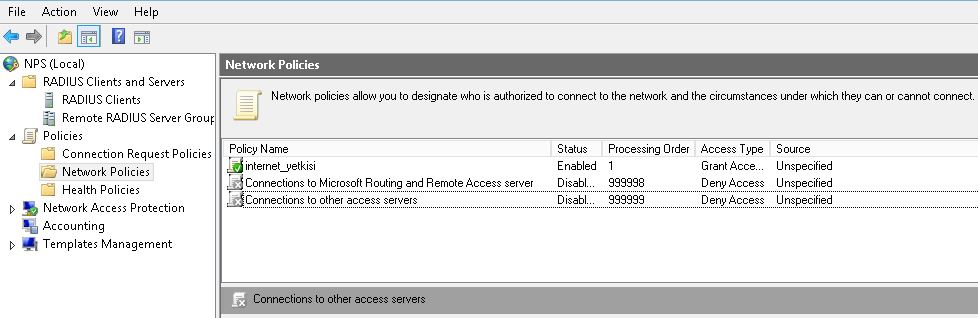
Here I leave them off because I work with the standard rules.
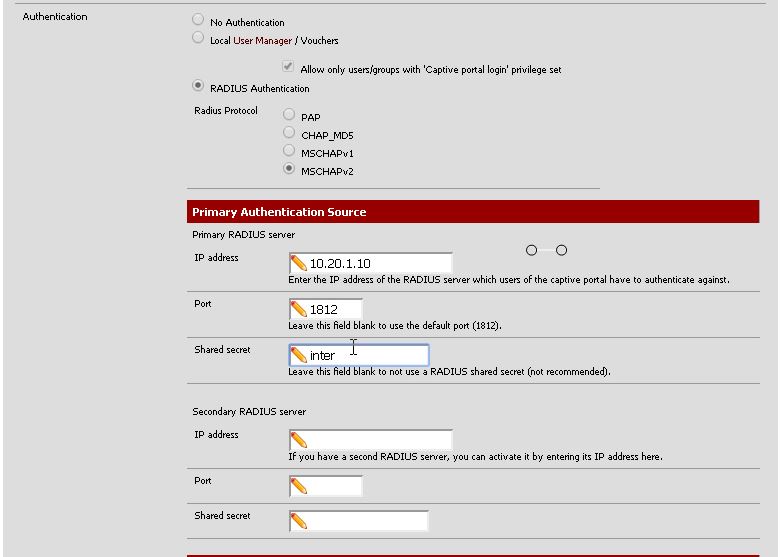
4-) On Pfsense Servers–>Captive portal–>New Zone saying, but here we are creating a new zone zone name in the name you give to the RADIUS server must be the same name you gave to the Radius client !!

Captive Portal Enable Network I choose whether I apply.

After Authentication URL Redirect: If you want the option to be automatically redirected after authentication can enter the site name.

Primary Authentication section
We choose the authentication method MSCHAPv2.
IP Address: enter the address of the server that I found my RADIUS server.
Port: Here you can enter idle to as 1812.
Shared secret: we have created a security key in this section Radius server
How do I choose the LAN network up my rope Radius attribute section.
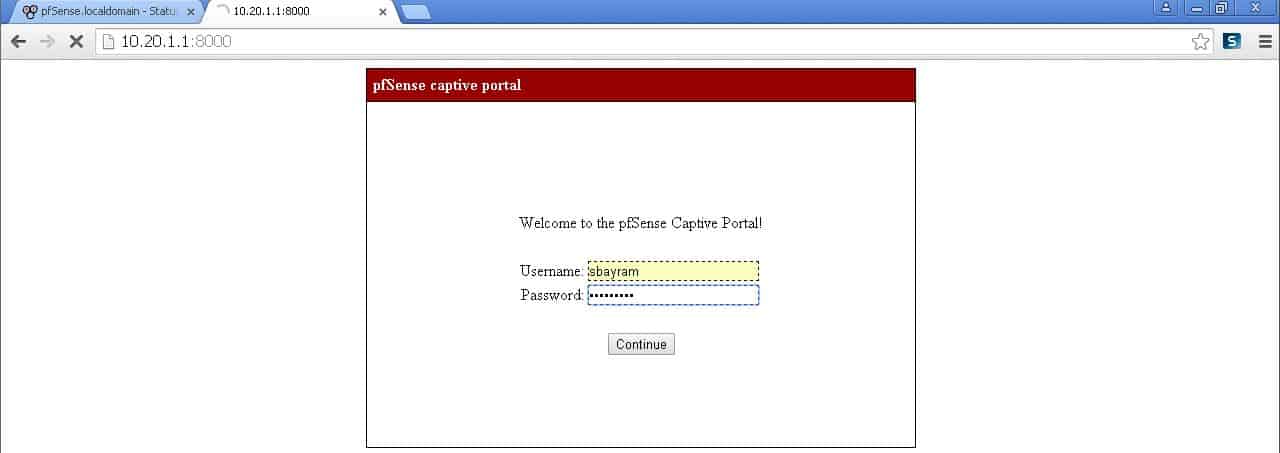
Yes my friends now configure all the settings that we now have on our users will no longer encounter with AD captive portal screen where they want to go to the internet and be able to provide their AD user name and password by entering the exit to the internet.

Internet users trying to go to meet our screen here by entering the user information that our users can go to the Internet as follows.

Captive Portal active on the dashboard by which users can perform follow that out to the internet.

Created by
Serdar BAYRAM